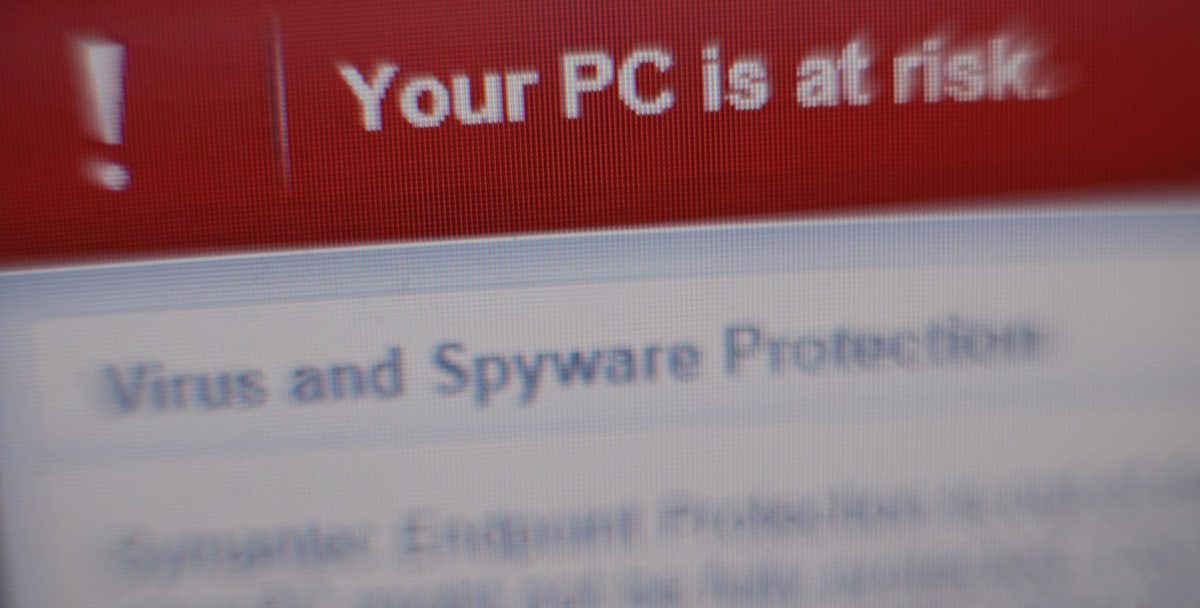
As Friday’s unprecedented “ransomware” cyberattack continues to cause crippling disruptions in nearly 100 countries across the globe, a noted cybersecurity expert is warning that these attacks are the wave of the future.
A wider spread of the Wanna Decryptor 2.0 malware was stopped by a quick-thinking 22-year-old British researcher, who bought the domain that housed the program’s kill switch. But there is nothing preventing the same hackers—or copycats—from trying again.
If even a fraction of the estimated 75,000-plus computer users hit by the attack paid the extortioners’ fee of $300 (in bitcoin) to unlock their computers, the heist could add up to millions, or even billions. And that’s too big a potential score for them, or for copycats, to ignore.
“It’s quite possible there will be a second wave,” says Edward M. Stroz, former FBI special agent, who formed the agency’s computer crime squad in New York.
“There’s nothing that happened here that would make this a prohibition,” Stroz, co-president of Stroz Friedberg, a corporate cybersecurity firm, told RealClearLife.
“The attack in of itself is wrong. It’s a criminal act. It should not be minimized. But the other part of it is, what about your defense? To what extent has the victimized organizations listened to the advice of the professionals to minimize their vulnerability and impact?”
Since the attacks themselves are nearly impossible to predict or stop, computer users must insulate themselves as much as possible.
RELATED: EDWARD M. STROZ ON CYBERATTACK THAT HIT TWITTER
“The reason why ransomware can be so effective is the machine or the device that is infected often has no backup to recover,” says Stroz.
“If you are prepared, you take that machine off-line, you reformat it and you restore the data you had on the reformatted machine or on a new machine and you’re recovered. But apparently a lot of places (hit by Friday’s cyberattack) were not doing this or running ancient software that can not be patched.”
Stroz tells his clients that the two major lessons are to 1.) keep operating systems software updated and patched in a timely manor and 2.) to back up data to avoid the risk of complete loss in the event of corruption.
Hit particularly hard in Friday’s attack was Britain’s National Health Service, as hospitals tend to rely on older computers and software because tech tends to get a lower priority in budgets.
“This technology can hurt you so much more than the amount of money you spent to buy it,” says Stroz. “So you can’t just say, ‘Would I spent $1000 to guard a $100 bill?’ No, you wouldn’t. But a $100 computer can become a $16 million problem because of the data that it holds.”
Apparently pilfered from a cyber-weapon designed by the NSA, Wanna Decryptor 2.0 spread quickly from Chinese universities, to the Russian Interior Ministry, to FedEx servers on this side of the Atlantic. But the United States was largely spared by that quick-thinking employee of Kryptos Logic, who told the Washington Post he paid just $10.69 to buy the domain after another cybersecurity expert found its name referenced in the malware code.
Call it educated luck.
“You look at all the blips on the map, and one of the factors that influenced the pattern of those blips was this researcher taking action in Europe and where that was in relation to time zone difference with the United States,” says Stroz.
Relying on good fortune, though, is not a good strategy when facing another cyberattack.
“We’ve been saying that ransomeware is going to be a bigger deal as time goes on,” says Stroz. “The Internet of Things (web-based technology in other products, such as appliances) is going to make it possible to deploy new kinds of attacks.
“Wayne Gretzky said the thing that made him good was that he always played to where the hockey puck was going, not where it was. Well, there’s a tendency in this world to always play where the hockey puck is, rather than where it’s going.”
This article appeared in an InsideHook newsletter. Sign up for free to get more on travel, wellness, style, drinking, and culture.